Kaspersky exposes NKAbuse, a multiplatform malware leveraging blockchain technology
Kaspersky’s Global Emergency Response Team (GERT) and Global
Research and Analysis Teams (GReAT) uncovered NKAbuse, a novel multiplatform
malware. This advanced threat, developed in Go, uses peer-to-peer
communication, functioning both as a flooder and a backdoor.
In a recent incident response analysis, Kaspersky’s experts
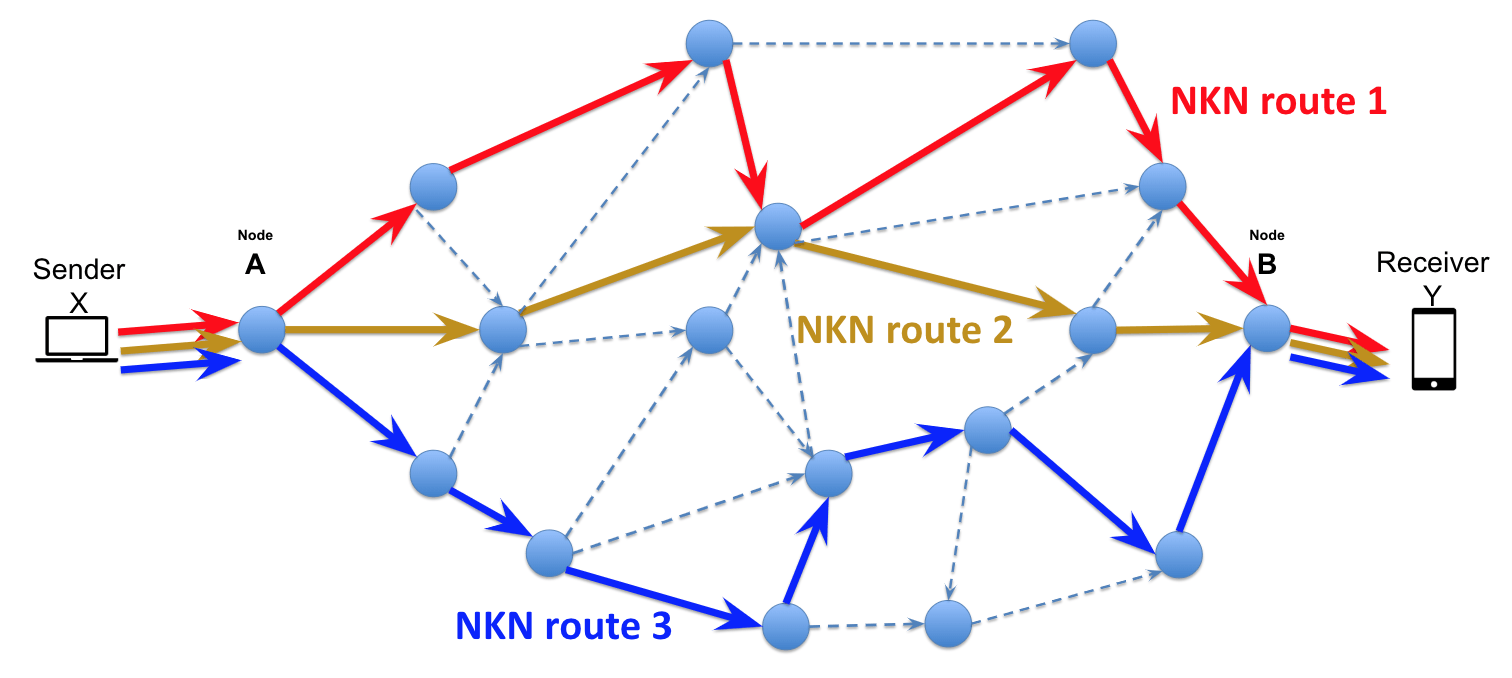
found a new malware that exploits NKN technology, a peer-to-peer,
blockchain-oriented networking protocol known for its decentralization and
privacy. Kaspersky Security Network identified potential victims of the attack
in Colombia, Mexico, and Vietnam.
NKAbuse is a hybrid implant that serves as both a backdoor/RAT
and a flooder, making it a versatile dual threat. In its backdoor/RAT role,
NKAbuse provides attackers with unauthorized access to victims’ systems
enabling the attacker to covertly execute commands, steal data, and monitor
activities. This feature is particularly valuable for espionage and data exfiltration.
Simultaneously, as a flooder, it is capable of launching destructive DDoS
attacks overwhelming and disrupting targeted servers or networks, significantly
impacting organizational operations.
The malware’s advanced features extend to capturing screenshots,
managing files, retrieving system and network information, and executing system
commands. The collected data is sent to its botmaster via the NKN network using
decentralized communications for stealth and efficiency.
NKAbuse's infiltration process begins by exploiting the old RCE
vulnerability CVE-2017-5638, allowing attackers to take over the affected
systems. After gaining control, the malware downloads an implant onto the
victim's host. This implant is initially placed in a temporary directory for
execution. NKAbuse then establishes persistence by creating a cron job and
situates itself within the host’s home folder, ensuring its continuous
operation within the system.
"The implant's use of the NKN protocol underlines its
advanced communication strategy, enabling decentralized, anonymous operations
and leveraging NKN's blockchain features for efficient, stealthy communication
between infected nodes and C2 servers,” says Lisandro Ubiedo, security
researcher at Kaspersky GReAT. “This approach complicates detection and
mitigation efforts. I would like to commend the Kaspersky GERT team for their
exceptional effort in identifying this sophisticated threat."
The choice of Go enables cross-platform compatibility allowing
NKAbuse to target various operating systems and architectures, including Linux
desktops and IoT devices. This programming language enhances the implant's
performance, particularly in networked applications, ensuring efficient and
concurrent processing. Moreover, Go's ability to produce self-contained
binaries simplifies deployment and enhances robustness, making NKAbuse a
formidable tool in the realm of cybersecurity threats.



























Leave A Comment